Pell Center Cybersecurity Roundtable Discussion Addresses Supply Chain Risks and Mitigation Strategies
NEWPORT, R.I.—The Pell Center hosted a cybersecurity roundtable discussion on April 7 in collaboration with New England’s premier electricity and gas utility company, National Grid, as part of its ongoing Rhode Island Corporate Cybersecurity Initiative (RICCI). This particular event explored some of the cybersecurity risks of working with third party vendors and how to evaluate and manage them to enable business objectives. Mr. Michael Andreozzi, IS Compliance Manager, and Mr. Scott Baron, Director, Governance Risk and Compliance at National Grid, examined important steps companies can take to identify risks of potentially insecure service providers, and options to mitigate those risks as part of their decision making process. They also engaged the audience in an open and frank discussion about third party management policies and strategies already in place in some of the other organizations represented in the room, from both the private and public sectors.

Image: Target
Defending against cyber-attacks is a complex and never-ending job and involves enterprise-wide strategies. As Mr. Baron said: “Cybersecurity in our day and age is like playing a football game, but we are always playing from the defense, and still have to win every single time!” Moreover, the long list of very public data breaches in the past year has shown that cyber attackers are increasingly targeting third party suppliers. Many, if not all, of last year’s successful data breaches began with attackers compromising a portion of the victim company’s supply chain as a way to get access to their clients’ information and possibly internal systems.
Working with third party vendors is almost inevitable in today’s dynamic and ever changing business environment; many companies use service providers to offer specialized services and additional capabilities, support decentralization and mobilization, increase users and customers experience, and provide scalability. 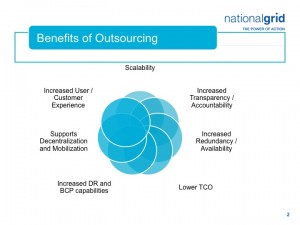 As Mr. Andreozzi said: “along with the benefits of outsourcing, however, come also additional risks that, if are not properly managed, can adversely impact an organization and result in damages to the brand, loss of investor and customer confidence, and financial or reputational harm.” All of this can have lasting effects and possibly result in companies’ failure to meet business objectives or worse. Yet, most companies fail to recognize those security risks or see the need to work proactively with the business, partners, and suppliers to reduce them.
As Mr. Andreozzi said: “along with the benefits of outsourcing, however, come also additional risks that, if are not properly managed, can adversely impact an organization and result in damages to the brand, loss of investor and customer confidence, and financial or reputational harm.” All of this can have lasting effects and possibly result in companies’ failure to meet business objectives or worse. Yet, most companies fail to recognize those security risks or see the need to work proactively with the business, partners, and suppliers to reduce them.
For any modern organization, physical supply-chain management already presents numerous complex challenges in understanding exposure to risk. The added complexity of cybersecurity risks only amplifies this, regardless of their position within a supply chain. National Grid has over 16,000 vendors, including suppliers to suppliers, and thus a very complex environment to manage.  In addition, as we move toward increasingly interconnected and modernized network systems, as is happening in the energy sector with Smart Grid, the potential for wide-scale impact creates a more attractive target for hacktivists and cyber criminals, who can either disrupt service or compromise databases and data transmissions. Recognizing the risks that cyber ‘insecurity’ can pose to their organization, and especially to the confidentiality, integrity, and availability of their key assets, National Grid has made cybersecurity an integral component of its security posture and has developed strategies that involve the entire business in a holistic manner. As Mr. Andreozzi said: “The threat landscape is always changing, and we know we have to stay always ahead of the threats. However, we can’t manage what we don’t know, so we have our own assurance frameworks to carry out third party risk assessments and make sure our vendors are being compliant with our guidelines and security controls.”
In addition, as we move toward increasingly interconnected and modernized network systems, as is happening in the energy sector with Smart Grid, the potential for wide-scale impact creates a more attractive target for hacktivists and cyber criminals, who can either disrupt service or compromise databases and data transmissions. Recognizing the risks that cyber ‘insecurity’ can pose to their organization, and especially to the confidentiality, integrity, and availability of their key assets, National Grid has made cybersecurity an integral component of its security posture and has developed strategies that involve the entire business in a holistic manner. As Mr. Andreozzi said: “The threat landscape is always changing, and we know we have to stay always ahead of the threats. However, we can’t manage what we don’t know, so we have our own assurance frameworks to carry out third party risk assessments and make sure our vendors are being compliant with our guidelines and security controls.”
 Both speakers emphasized a common theme in RICCI events—that it is the leaders’ responsibility within their organizations to work with the business to understand and minimize the risks those suppliers and service providers can introduce along with their services. Additional best practices that National Grid has implemented to manage suppliers include:
Both speakers emphasized a common theme in RICCI events—that it is the leaders’ responsibility within their organizations to work with the business to understand and minimize the risks those suppliers and service providers can introduce along with their services. Additional best practices that National Grid has implemented to manage suppliers include:
- Carrying out risk assessments with all suppliers, including auditing and onsite assessments. As Mr. Baron stated: “You probably shouldn’t move forward with a contractor who does not want to be audited or complete assurance reports.”
- Following procurement processes with an emphasis on cybersecurity risks.
- Conducting thorough due diligence for new suppliers, including using in-house security consulting teams with pen testers that can identify issues with new vendors and account for their cybersecurity competence; and employ legal teams to work on specific contracts with different vendors.
- Considering contractual clauses with set standard terms and conditions that cover security, confidentiality, privacy, and compliance; stipulating responsibility for any compromise or data breach by holding the main provider accountable for it; and contractually mandating that security clauses apply to sub-contractor(s) in the supply chain.
- Conducting regular information-assurance sessions to identify weak links.
The biggest takeaway, however, was that having business continuity and resiliency plans in place, with redundancies and multiple layers of resiliencies built in the system, remains fundamental. Reliability in the utility industry, even at the detriment of security, is key.
For more information on the Pell Center cybersecurity initiative and future events, visit the RICCI webpage or contac t the Pell Center at [email protected].
The Rhode Island Corporate Cybersecurity Initiative is supported by The Verizon Foundation for the 2014-2015 academic year.


