Pell Center Lecture Discusses U.S Government and Private Sector Cybersecurity Efforts, the Impacts of the NIST Framework
NEWPORT, R.I.—The Pell Center hosted a major cybersecurity lecture this month that featured Roger Cressey, an internationally known cybersecurity expert and counterterrorism analyst with NBC News, and Kiersten Todt, President and Managing Partner of Liberty Group Ventures, LLC.
Over 50 senior leaders representing Rhode Island’s private and public sectors took part in the event to discuss cyber risk management and the impacts of the National Institute of Standards and Technology’s (NIST) National Cybersecurity Framework one year after its release.
 Mr. Cressey praised the Pell Center’s ongoing Rhode Island Corporate Cybersecurity Initiative (RICCI), which has become the de facto venue for major RI companies and state agencies—including Raytheon, Citizens, CVS, IBM, Mass Mutual, National Grid, RI Emergency Management Agency, RI State Police, as well as the U.S. Attorney’s office—to discuss some of the most pressing cybersecurity issues, share information, and encourage cybersecurity best practices. Cressey encouraged leaders to continue to engage in these types of discussions to maximize Rhode Island’s potential to become a cybersecurity incubator and role model for other states.
Mr. Cressey praised the Pell Center’s ongoing Rhode Island Corporate Cybersecurity Initiative (RICCI), which has become the de facto venue for major RI companies and state agencies—including Raytheon, Citizens, CVS, IBM, Mass Mutual, National Grid, RI Emergency Management Agency, RI State Police, as well as the U.S. Attorney’s office—to discuss some of the most pressing cybersecurity issues, share information, and encourage cybersecurity best practices. Cressey encouraged leaders to continue to engage in these types of discussions to maximize Rhode Island’s potential to become a cybersecurity incubator and role model for other states.
 Mr. Cressey and Ms. Todt provided a compelling overview of the increasingly complex cyber threat environment and defined it as “an arms bazaar of attack code and weapon grade arsenal,” including over 300 new malware programs discovered daily, enhanced cyber tactics, techniques and procedures (TTPs), an incredibly profitable black market, and the growing threat of data destruction and manipulation. They detailed some of the most common cybersecurity challenges to the private sector, such as the expansion of the attack surface due to the increased use of mobile devices, web applications, social engineering techniques, and the advent of the Internet of Things (IoT). They also focused on the growing cyber risks from accidental and premeditated insider threats and third party vendors, as the supply-chain often presents multiple opportunities for adversaries to penetrate networks and it is increasingly the vector of choice for hackers to access corporate systems. “Don’t throw money at the problem after a breach happens,” Mr. Cressey stressed. “It’s time to invest in cyber before an attack, not after. What we need is a change of corporate culture and a shift of mindset from prevention to resiliency that requires management buy-in and attention from the C-suite. Treat cybersecurity as a risk equal in importance to other business risks—financial, brand, reputation, and integrity. And plan for the inevitable breach… it will happen… and most likely has already happened.”
Mr. Cressey and Ms. Todt provided a compelling overview of the increasingly complex cyber threat environment and defined it as “an arms bazaar of attack code and weapon grade arsenal,” including over 300 new malware programs discovered daily, enhanced cyber tactics, techniques and procedures (TTPs), an incredibly profitable black market, and the growing threat of data destruction and manipulation. They detailed some of the most common cybersecurity challenges to the private sector, such as the expansion of the attack surface due to the increased use of mobile devices, web applications, social engineering techniques, and the advent of the Internet of Things (IoT). They also focused on the growing cyber risks from accidental and premeditated insider threats and third party vendors, as the supply-chain often presents multiple opportunities for adversaries to penetrate networks and it is increasingly the vector of choice for hackers to access corporate systems. “Don’t throw money at the problem after a breach happens,” Mr. Cressey stressed. “It’s time to invest in cyber before an attack, not after. What we need is a change of corporate culture and a shift of mindset from prevention to resiliency that requires management buy-in and attention from the C-suite. Treat cybersecurity as a risk equal in importance to other business risks—financial, brand, reputation, and integrity. And plan for the inevitable breach… it will happen… and most likely has already happened.”
 First and foremost, however, companies need to understand their interdependencies and threat environment. Ms. Todt explained that one of the main issues with detecting an attack is that most companies do not have a centralized procedure in place to process all the information and potential red signs that they see on their networks. “Companies are drowning in data, but starving for information,” she said. “They must establish processes across the enterprise to identify threat-critical data. Employee education is the foundation of corporate cybersecurity—they are both your weakest link and your first line of defense. Companies should also establish threat information-sharing policies and have a cyber risk management plan in place—managing cyber risk means understanding that you will be breached and knowing how to mitigate the breach.”
First and foremost, however, companies need to understand their interdependencies and threat environment. Ms. Todt explained that one of the main issues with detecting an attack is that most companies do not have a centralized procedure in place to process all the information and potential red signs that they see on their networks. “Companies are drowning in data, but starving for information,” she said. “They must establish processes across the enterprise to identify threat-critical data. Employee education is the foundation of corporate cybersecurity—they are both your weakest link and your first line of defense. Companies should also establish threat information-sharing policies and have a cyber risk management plan in place—managing cyber risk means understanding that you will be breached and knowing how to mitigate the breach.”
Their main recommendation was to use the NIST Framework to create a profile that would help their respective organizations understand their dependencies with business partners, vendors, and suppliers, and then to follow the set of cybersecurity guidelines to better identify, protect, detect, respond, and recover from cyber threats. “The Framework is your friend,” said Mr. Cressey, “it provides your organization a template to track efforts for cybersecurity practices.”
The blueprint for the Framework grew out of President Obama’s Executive Order on “Improving Critical Infrastructure Cybersecurity,” in which he directed the National Institute of Standards and Technology (NIST) to work with various stakeholders to develop a comprehensive approach towards mitigating cyber risks to critical infrastructure. 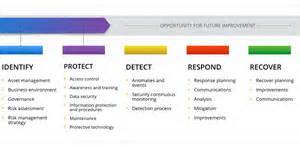 The Framework, “a product of industry, not government,” as Mr. Cressey emphasized, creates a common language for cybersecurity within and across sectors, applies a market-driven approach to cyber risk management, and provides a set of voluntary standards, guidelines, and best practices for cybersecurity. Since its release, the Framework has facilitated behavioral change in organizations, encouraged them to examine and understand key priorities and vulnerabilities, and supported cyber resiliency within and across sectors. All throughout 2014 and 2015, critical industry sectors have taken steps to align their own security guidance to the Framework, and U.S. federal agencies and departments—as well as state governments and associations—have engaged and embraced the Framework as the key standard for the various industries that they regulate.
The Framework, “a product of industry, not government,” as Mr. Cressey emphasized, creates a common language for cybersecurity within and across sectors, applies a market-driven approach to cyber risk management, and provides a set of voluntary standards, guidelines, and best practices for cybersecurity. Since its release, the Framework has facilitated behavioral change in organizations, encouraged them to examine and understand key priorities and vulnerabilities, and supported cyber resiliency within and across sectors. All throughout 2014 and 2015, critical industry sectors have taken steps to align their own security guidance to the Framework, and U.S. federal agencies and departments—as well as state governments and associations—have engaged and embraced the Framework as the key standard for the various industries that they regulate.
The Framework has also sparked an enhanced national debate about related controversies regarding cybersecurity and the controls necessary to improve it.
 Last year, the Pell Center organized the first event of its kind hosted in New England after the release of the Framework in February 2014—a panel discussion on “Improving Critical Infrastructure Cybersecurity: The National Cybersecurity Framework and Beyond.” The panel discussed the specifics of the NIST Framework and other national and state initiatives to support its implementation. The distinguished speakers from both the federal and state government—including Adam Segewick, NIST senior information technology policy advisor; Michal Leking, the Department of Homeland Security’s cybersecurity advisor for the Northeast region; and Jamia McDonald, former executive director of the state’s Emergency Management Agency—explored how organizations charged with providing the nation’s financial, energy, healthcare, and other critical systems could use the Framework to better protect their information and physical assets from cyber attacks.
Last year, the Pell Center organized the first event of its kind hosted in New England after the release of the Framework in February 2014—a panel discussion on “Improving Critical Infrastructure Cybersecurity: The National Cybersecurity Framework and Beyond.” The panel discussed the specifics of the NIST Framework and other national and state initiatives to support its implementation. The distinguished speakers from both the federal and state government—including Adam Segewick, NIST senior information technology policy advisor; Michal Leking, the Department of Homeland Security’s cybersecurity advisor for the Northeast region; and Jamia McDonald, former executive director of the state’s Emergency Management Agency—explored how organizations charged with providing the nation’s financial, energy, healthcare, and other critical systems could use the Framework to better protect their information and physical assets from cyber attacks.
One year later, the Framework continues to be increasingly used and lists among its greatest benefits the establishment of a common language, collaboration opportunities, the ability to demonstrate due care in adopting the Framework, the ability to promote better security within the vendor supply chain, and cost efficiency in cybersecurity spending. In addition, as more U.S. federal agencies and state governments adopt the Framework, and strongly encourage private sector organizations to implement its approach, there can be little doubt that the Framework has or will soon evolve into the de facto standard for cybersecurity. It may remain a voluntary undertaking, but it seems clear it will become the standard against which all other developments are measured.
For more information on the Pell Center cybersecurity initiative and future events, visit the RICCI webpage or contact the Pell Center at [email protected].
The Rhode Island Corporate Cybersecurity Initiative is supported by The Verizon Foundation for the 2014-2015 academic year.

