Pell Center Seminar Addresses Key Skills and Knowledge of Effective Chief Information Security Officers (CISOs)
 NEWPORT, R.I.—The world’s first Chief Information Officer (CIO) and renowned cybersecurity expert, Mr. Steve Katz, led the recent seminar on “Cybersecurity and Corporate Leadership: Connecting the Server Room and the Board Room” at the Pell Center. The event, held on October 14, kicked off the second year of the Pell Center’s Rhode Island Corporate Cybersecurity Initiative (RICCI), which was launched in 2013 and aims to bring together senior leaders from various industries—defense, financial services, technology, healthcare, etc.—who can affect change and make Rhode Island’s corporate community a national model of cybersecurity leadership. Timed to coincide with the annual National Cybersecurity Awareness Month,
NEWPORT, R.I.—The world’s first Chief Information Officer (CIO) and renowned cybersecurity expert, Mr. Steve Katz, led the recent seminar on “Cybersecurity and Corporate Leadership: Connecting the Server Room and the Board Room” at the Pell Center. The event, held on October 14, kicked off the second year of the Pell Center’s Rhode Island Corporate Cybersecurity Initiative (RICCI), which was launched in 2013 and aims to bring together senior leaders from various industries—defense, financial services, technology, healthcare, etc.—who can affect change and make Rhode Island’s corporate community a national model of cybersecurity leadership. Timed to coincide with the annual National Cybersecurity Awareness Month, the ongoing initiative provides a forum where public and private sector lead4ers can discuss ways to make their organizations—and thus Rhode Island—safer, more secure, and resilient in an increasingly hostile cyber environment. Initiatives like RICCI help maintain Rhode Island’s position at the vanguard of cybersecurity leadership.
the ongoing initiative provides a forum where public and private sector lead4ers can discuss ways to make their organizations—and thus Rhode Island—safer, more secure, and resilient in an increasingly hostile cyber environment. Initiatives like RICCI help maintain Rhode Island’s position at the vanguard of cybersecurity leadership.
This particular seminar focused on one critical issue: the need for corporate leaders to be fully informed about how cyber-risk issues are being addressed within their companies. As part of that necessity, the seminar outlined the skills and knowledge the increasingly-necessary Chief Information Security Officer (CISO) should have, especially the ability to communicate cybersecurity issues effectively and to build relationships with the C-suite. As Mr. Katz emphasized, “information security is both a business risk management and governance issue that connects technology, business management, and the board room.” There is an increasingly clear link between cyber attacks and their impact on customers, brand, revenue, and profits. The risk is so great that plausible deniability, lack of awareness about information risk, and treating information security as a mere technology problem are no longer acceptable or effective options. A strong cybersecurity posture requires ownership and responsibility from the top down. CEOs and boards of directors are accountable for the health of their organizations and for setting levels of risk tolerance for their companies. They are also responsible for building a team of trusted information security professionals who will not only implement a program that meets risk and governance requirements but also routinely report on the company’s cybersecurity posture. Failure to do so can be analogized to a dereliction of duty in a cybersecurity environment brimming with threats.
To counter these threats effectively, CISOs play a key role in assuring that a security plan is successfully developed and implemented within their company. Before they can do that, however, they must first and foremost understand the business they are in and how to integrate security into business, and business into security. After all, “technology doesn’t have risks,” said Mr. Katz, “businesses do! They need to understand what is the business problem that they are trying to address and identify the ‘whys’ and ‘hows’.” And the cybersecurity issue still has its critical human component. As Mr. Katz reminded the audience, “today’s first line of defense is still human intelligence.” “Information security professionals must constantly monitor transactions and look for abnormal activity […] Detection is key, and an effective CISO must be able to prevent, detect, and respond to a wide array of cyber threats.” At the same time, he must be able to “obtain the resources to meet yesterday’s, today’s, and tomorrow’s threats,” which in turn requires building trust and cultivating relationships with the boardroom and the risk management people. “The CISOs runs a company within a company,” Mr. Katz stressed.
In addition, CISOs core responsibilities must include: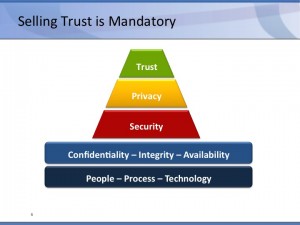
- Developing and maintaining confidence, both internally and externally—“the CISO has to become a trusted advisor.”
- Ensuring the confidentiality, integrity, and availability of information and services—verticals make a difference;
- Having enough visibility into the enterprise to know where, why, and how to spend budget dollars, and optimizing the cost of information security without significantly increasing risk;
- Knowing where to focus security efforts—prioritizing. “Nothing is ever going to be 100% secure and you can’t secure everything.”
- Demonstrating risk benefit of existing and planned budgets, and measuring the effectiveness of the program;
- Enabling the pursuit of business opportunities while meeting regulatory, trust, security, and privacy commitments;
- Establishing information risk management paradigm, and communicating the value of making security investments;
- Fostering company-wide education, awareness, and training;
- Measuring success through regular risk assessments, continuous improvement, and ongoing processes to continually test and upgrade incident detection, investigation, and response activities;
- Assuring that security products, tools, technologies, and processes are implemented, operational, and monitored; and
- Regularly briefing executives on Board level risk assessments and state of security program.
 Mr. Katz then provided the attendees with a set of practical, non-technical questions that CISOs should ask when meeting with business executives to establish the specific challenges that need to be addressed, what needs to be prioritized, and how to reach a set of goals.
Mr. Katz then provided the attendees with a set of practical, non-technical questions that CISOs should ask when meeting with business executives to establish the specific challenges that need to be addressed, what needs to be prioritized, and how to reach a set of goals.

Finally, he gave an overview of some of the top security challenges for the year 2014/2015—including mobile security, application security, Internet of Things, etc.—and reminded people that “When we stop getting better, we stop being good!”
For more information on the initiative and future events, visit the RICCI webpage or contact the Pell Center at [email protected] or 401-341-2927.
The Rhode Island Corporate Cybersecurity Initiative is supported by The Verizon Foundation for the 2014-2015 academic year.

