Status Update: I’ve been Hacked!
Chances are high that, at some point today, either you or someone you know has posted an online message through one of the many social media platforms available. Hundreds of millions of users flocked to social networks this year to do precisely that, and they are doing it in record numbers though smart-phones, tablets, or desktop computers. The problem, however, is that this development has been noticed by one group in particular—hackers and cyber-attackers.
 The prime target for these individuals is perhaps the most obvious: Facebook. With over a billion users worldwide, Facebook commands a veritable gold mine of information and, like insects within range of a lightbulb, the hackers just can’t stay away. In fact, one need not be a hacker—or expert programmer—to get started. A simple Google search yields countless websites that offer software (really malware) and multiple tips and tricks on how to hack into Facebook accounts to steal information or download infected software into the victim’s computer (don’t try this at home, or elsewhere!).
The prime target for these individuals is perhaps the most obvious: Facebook. With over a billion users worldwide, Facebook commands a veritable gold mine of information and, like insects within range of a lightbulb, the hackers just can’t stay away. In fact, one need not be a hacker—or expert programmer—to get started. A simple Google search yields countless websites that offer software (really malware) and multiple tips and tricks on how to hack into Facebook accounts to steal information or download infected software into the victim’s computer (don’t try this at home, or elsewhere!).
 Earlier this year, scammers took advantage of the widespread skepticism about Facebook’s new Timeline feature to trick users into clicking different links that purported to remove the feature. Those who followed the instructions were taken to a page that looked like Facebook but was not. This faux-Facebook page encouraged users to ‘Continue’ or ‘Like’ or ‘install’ various items just like the real Facebook, and those who fell for this trap automatically became victims of click-jacking or like-jacking, because the bogus link then spread on their personal Facebook Walls. When their friends noticed the link and clicked it themselves, the hacking process simply repeated itself.
Earlier this year, scammers took advantage of the widespread skepticism about Facebook’s new Timeline feature to trick users into clicking different links that purported to remove the feature. Those who followed the instructions were taken to a page that looked like Facebook but was not. This faux-Facebook page encouraged users to ‘Continue’ or ‘Like’ or ‘install’ various items just like the real Facebook, and those who fell for this trap automatically became victims of click-jacking or like-jacking, because the bogus link then spread on their personal Facebook Walls. When their friends noticed the link and clicked it themselves, the hacking process simply repeated itself.
Another common exploit has been using the users’ natural worries about newly posted images or videos of themselves to lure the recipient into viewing direct messages (DMs), purportedly from online friends, reporting that they had been captured in a Facebook video.  These DMs, usually spammed out from newly-compromised Twitter accounts, tricked the unwary into clicking the link they contained, which would take the users to a website telling them to upgrade their “YouTube player.” If the user went further, they would be infected with the Troj/Mdrop-EML, detected by Sophos as a backdoor Trojan that can also copy itself to accessible drives and network shares. Exactly how the Twitter accounts were compromised and able to send malicious DMs remains unclear, but the attack underscores a key message about modern social media security: if a friend sends you a link, don’t click it without thinking!
These DMs, usually spammed out from newly-compromised Twitter accounts, tricked the unwary into clicking the link they contained, which would take the users to a website telling them to upgrade their “YouTube player.” If the user went further, they would be infected with the Troj/Mdrop-EML, detected by Sophos as a backdoor Trojan that can also copy itself to accessible drives and network shares. Exactly how the Twitter accounts were compromised and able to send malicious DMs remains unclear, but the attack underscores a key message about modern social media security: if a friend sends you a link, don’t click it without thinking!
 If you do find that it was your Twitter account sending out the messages, the sensible course of action is to assume the worst, change your password and revoke permissions of any suspicious applications that have access to your account.
If you do find that it was your Twitter account sending out the messages, the sensible course of action is to assume the worst, change your password and revoke permissions of any suspicious applications that have access to your account.
Finally, we have the usual phishing attempts to lure you into entering your account information into a web site that looks like the Facebook’s sign-in page or other web sites proclaiming offers for freebies of various kinds. Facebook has a page about how to avoid phishing. It also has a page about what to do if you’re locked out of your own account, but I recommend that you avoid this page unless you have actually been hacked, particularly if you are a Facebook user who is logged in. The site assumes that you’ve been attacked, and unless you hit “cancel”—one of two options you’ll have—you will be forced to change your password and security question. And you’ll learn very little about the hacking problem.
So, what can we do to protect the information we post online—the pictures of cats, the live-blog of what we’re eating for lunch, etc.—from those who wish us (digital) harm?
The good news is that you don’t have to de-friend everyone you know for fear they will start sending you malicious links or software. The better news is that there are various concrete steps you can take today to better protect your online information. You should:
- Choose a strong password. Include cr@zy symbols, some numb3rs, and even a ma+hematical sign or two. Also be sure to include both uppercase and lowercase LeTtErS. Once you have established your password, do not share it with anyone.
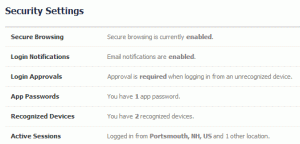
- Look over the privacy and security settings regularly and carefully choose your configuration:
- Secure Browsing – enabled
- Login Notifications – enabled
- Login Approvals – enabled
- Recognized Devices – if there is anything listed here that doesn’t look familiar, or the date is not recent, remove it
- Active Sessions – remove all except Current session.
- Take care when downloading applications and check the terms of use before you do. Yes, those long terms of use where you normally click on “Accept” without actually reading them!
- Only befriend people you know
- Report suspicious activity to Facebook
- Don’t post pictures, updates or the location where you are, if there is anybody in the world you would not want to be able to find out about it
Words of Wisdom: What we tend to forget is that the basic (unsecured) designs underpinning the Internet were built on presumptions of good intentions and not with the numerous possibilities of malevolent sabotage in mind. Indeed, the original internet inventors, developers and planners engineered the Internet to enhance wealth and the free and easy exchange of ideas and information, and assumed that new participants would automatically adapt to established rules of the road based on social trust, the security of property and the best use of this technology for the greater good. But where great value in goods, knowledge and funds flows without societal protection (or a much more complex, secured and encrypted system), so grows great potential for crime and conflict, even in cyberspace.