The Human Side of Cybercrime (OpEd)
What do cyber criminals, Greek gods, and Facebook have in common? They are all connected to “Zeus,” a Trojan horse malware program first identified in 2007, when it was used to steal information from the U.S. Department of Transportation, and that now may be lurking in a link on rigged Facebook pages.
Along with phishing campaigns, Trojans are the principal method chosen by cyber criminals to attack users, allowing them steal personally identifiable information and manipulate online transactions. The scary part is that all it takes is a single click to allow this silent thief to sneak into your computer. Zeus Trojans and variants of these are currently the most common programs used to launch such attacks, especially in the area of bank customer fraud. Once the program has infiltrated a system, the virus remains dormant until the user logs into a bank network, after which it steals the person’s username and password and drain his/her account. It can also generate cloned bank websites, which it uses to collect sensitive data—such as Social Security numbers or credit card information—that can later be sold on the black market.
Given the risks involved and the increasing public awareness of cybercrimes online, how exactly can Trojans like Zeus spread so easily online? The prime target for these trojans, as with other common exploits described in previous posts, is Facebook.  With over one billion users worldwide, Facebook commands a veritable gold mine of information and allows anyone—from me and you to hackers and cyber criminals—to create profiles, news, and ads. A valid email address remains the only requirement to create an account there. At the same time, hundreds of legitimate businesses have flocked to social media platforms in recent years, especially Facebook, to promote their brands and sell their products. Since these companies often establish pages with an eye towards increasing their number of followers and ‘likes,’ they are less focused on protecting customer information and managing potential risk on Facebook. A relaxed security posture, compounded with the absence of meaningful risk controls within these social media platforms, have together made social media a veritable El Dorado for cyber criminals to exploit social networks and the inherent trust placed in these networks. Generally, all you need is a phony Facebook page to lure users into clicking an infected link on a seemingly legitimate page, and the Trojan Zeus can get to work.
With over one billion users worldwide, Facebook commands a veritable gold mine of information and allows anyone—from me and you to hackers and cyber criminals—to create profiles, news, and ads. A valid email address remains the only requirement to create an account there. At the same time, hundreds of legitimate businesses have flocked to social media platforms in recent years, especially Facebook, to promote their brands and sell their products. Since these companies often establish pages with an eye towards increasing their number of followers and ‘likes,’ they are less focused on protecting customer information and managing potential risk on Facebook. A relaxed security posture, compounded with the absence of meaningful risk controls within these social media platforms, have together made social media a veritable El Dorado for cyber criminals to exploit social networks and the inherent trust placed in these networks. Generally, all you need is a phony Facebook page to lure users into clicking an infected link on a seemingly legitimate page, and the Trojan Zeus can get to work.
The uptick in Zeus-serving malicious links has been brought to my attention on an almost daily basis by Eric Feinberg, founder of the advocacy group Fans Against Kounterfeit Enterprise (FAKE) and the company EyeOn, which helps major brands and firms manage their social media presence and ensure their brand is safeguarded against counterfeiting.
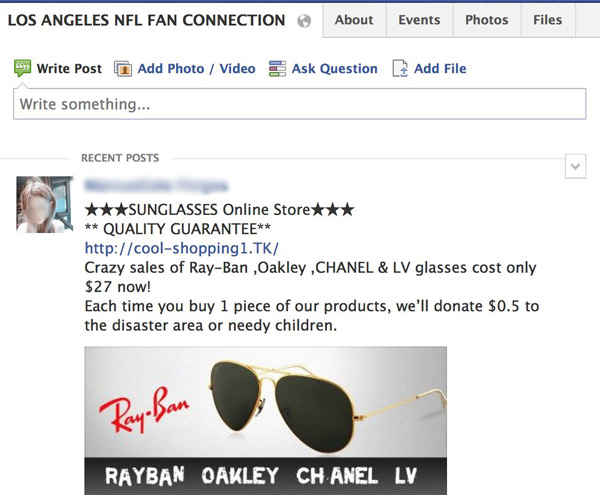
“The first red flag should be the url ending in .TK”
Mr. Feinberg has noticed most of this malicious activity on popular NFL Facebook fan pages, but also websites selling counterfeit merchandise from NFL, MLB, NBA, and NCAA teams, and major luxury brands as well. According to Trend Micro, the pages are being hosted by the Russian criminal gang known as the Russian Business Network, which has been linked to various online criminal activities, ranging from malware to identity theft to child pornography.
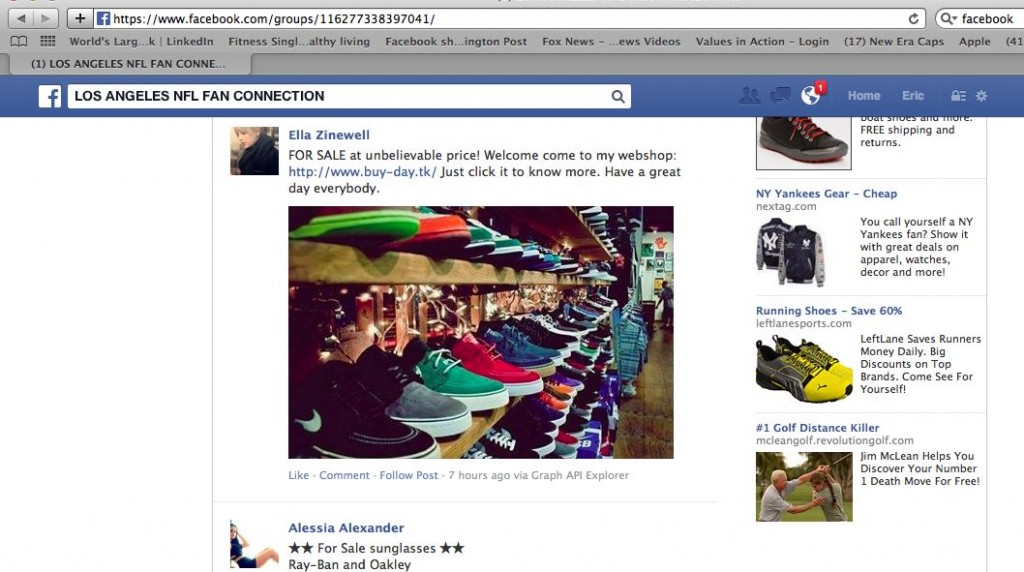
Ella Zinewell, for example, is one of the fake Facebook profiles that posts links to Internet addresses controlled by the Russian Business Network to spread the malicious Zeus malware.
Mr. Feinberg has tried to push Facebook to take stronger measures against these bogus links and the rampant spread of malware. Unfortunately, he says that “Facebook is not taking it seriously and is just telling users to get their own antivirus solution, instead of putting human intelligence to the problem.” He stresses that an after-the-fact approach is insufficient. Effective cybersecurity must synthesize both human oversight and mitigation measures—you cannot simply call your local IT department to ‘fix’ the issue after the fact.
“What most articles written in recent weeks about the Facebook Zeus malware, including on The New York Times, are missing” added Mr. Feinberg, “is that these nefarious enterprises are using human beings to spread malware and counterfeiting with social engineering techniques, and that new software or antivirus alone are not going to stop it.” Indeed, cybersecurity efforts often fail to address the underlying questions: Who is trying to get in, and why? How do they respond to different opportunities and vulnerabilities in cyberspace? How will understanding these phenomena help us better protect ourselves and our valuable online information? How can we best train an effective cyber workforce that can identify malicious human behaviors in cyberspace?
During all of our conversations, Mr. Feinberg emphasizes the importance to use human intelligence and a new cadre of “cyber warriors” or “cyber counterintelligence” to effectively fight cybercrime. These individuals must not only have a deep understanding of programming, reverse engineering, social media algorithms, and search engine optimization, but should also be able to analyze human behaviors, recognize patterns, and investigate the digital environment for clues of criminal activities. Placing more emphasis on the development of specialized cybersecurity programs that include principles of criminological and engineering methods, but also the study of social sciences and behavioral psychology is imperative. At the same time, new career paths, specific accreditation standards, and appropriate professional certifications ought to be created for corporations, law enforcement, and local governments, among others, to tap into this valuable new workforce.
Perhaps a place to start is within our criminal justice programs, which traditionally
combine the principles of sociology, law, psychology, and public administration, but very seldom include analysis of the ethical, legal, cultural, and technical issues posed by cybercrimes.  Indeed, as underscored in my recent report, “One Leader at A Time: The Failure to Educate Future Leaders for an Age of Persistent Cyber Threat,” only few criminal justice programs in the country have started to add a cyber criminology component to their curricula. The good news is that a handful of universities—such as Salve Regina University and the University of Maryland—are now paving the way toward the creation of new cybersecurity concentrations within their criminal justice programs, in response to the needs of homeland security, law enforcement, and criminal justice in the 21st century.
Indeed, as underscored in my recent report, “One Leader at A Time: The Failure to Educate Future Leaders for an Age of Persistent Cyber Threat,” only few criminal justice programs in the country have started to add a cyber criminology component to their curricula. The good news is that a handful of universities—such as Salve Regina University and the University of Maryland—are now paving the way toward the creation of new cybersecurity concentrations within their criminal justice programs, in response to the needs of homeland security, law enforcement, and criminal justice in the 21st century.
In the meantime, protect yourself from the wide reign of Zeus by being very careful who you accept friend requests from, avoiding websites that contain the .TK extension (first red flag) and other bogus discount sites, and being smart about your social networking, especially if you are a big fan of football.
